MENU

Mission
Tailored IT Solutions with Tiered Complete Care Plans
At X Base, we understand that no two businesses are the same, which is why our Managed IT solutions are never cookie-cutter. Instead, we offer tiered Complete Care Plans-Cyber Guard, Cyber Shield, and Cyber Defense-tailored to your business’s unique needs.

Our Complete Take on Database Security
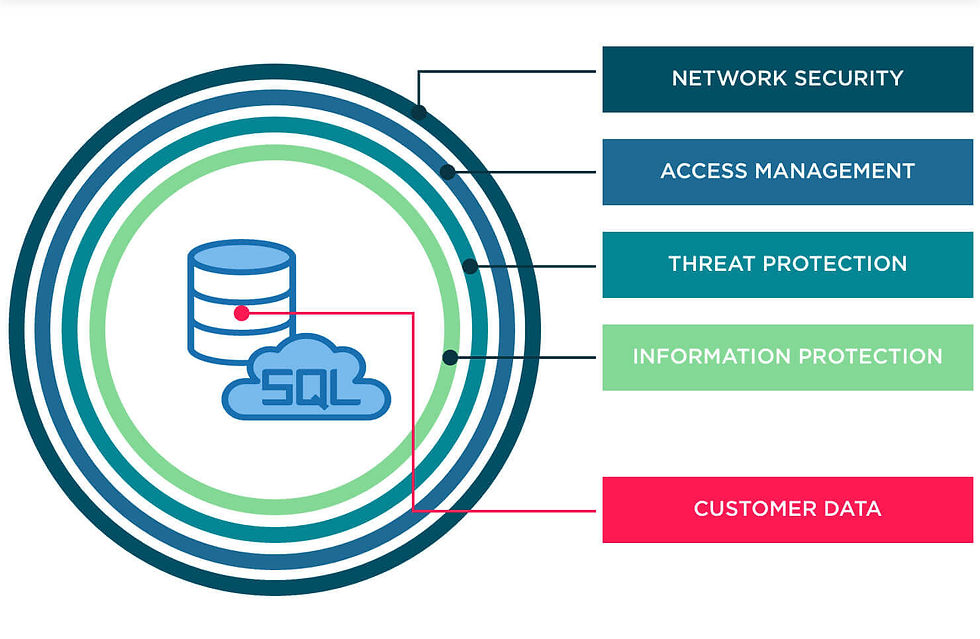
Database security unitestructure, edited safety settings, permissions, and access controls.
-
Authentification: each database should be automatically verifying user access to settings, networks, and data;
-
Backups: a safe database is always an audited mechanism for backup creation and management. Even if data is compromised or deleted, you will always have a copied version.
-
Encryption: implementing file encryption protects the contents of the file from being understood and utilized by cybercriminals. Even if they get access to the database, the information itself won’t be displayed.
What is database security?
Database security unites all protection activities performed on the database management system. It’s responsible for the data layer of software architecture, its processing, transfer, and storage. The main components of database security are:
-
Setting up security controls: database management systems usually offer custom systems of security assurance and monitoring. Developers need to edit the settings.
-
Configuration of a DBMS: security requires an organized data structure, edited safety settings, permissions, and access controls.
-
Authentification: each database should be automatically verifying user access to settings, networks, and data;
-
Constant database audit: monitoring database safety helps to catch security errors in time, reducing the impact of a breach, and detect suspicious patterns.
-
Backups: a safe database is always an audited mechanism for backup creation and management. Even if data is compromised or deleted, you will always have a copied version.
-
Encryption: implementing file encryption protects the contents of the file from being understood and utilized by cybercriminals. Even if they get access to the database, the information itself won’t be displayed.

Importance of Database Security
Over the last few years, we’ve seen what happens when businesses fail to keep their sensitive information secure. Only in April of 2020 Godaddy, the Dutch Government, United Nations, and Defense Information Systems Energy had data leaks. With an increased percentage of remote work and data access, the chances of compromising corporate and organization security grows. Big data breaches, like the ones in Uber or Equifax, make history and impact the company’s reputation long-term. Even an insignificant security crisis can have drastic consequences for the business.
-
Compromising secret practices: if your company has unique technological inventions, creative work, strategic documentation, or trade secrets, the breach of this data will weaken your presence on the market and potentially strengthen competitors.
-
Ruining reputation: today, many companies position safety as their main competitive advantage. Users become increasingly more aware of security risks and prefer cooperating with trusted businesses. Harris Poll survey showed that for 63% of people safety is a crucial factor in deciding on a purchase.
-
Facing legal consequences: governments become aware of indecent data storage practices and push them on the legal level. HIPAA, Payment Card Security Standards, GDPR have million-worth fines for compromising user data.
-
Bottlenecks: for data-based businesses, a breach means impossibility to continue their work and turn into downtime.
-
Additional expenses: dealing with a safety crisis is a lot more expensive than preventing it. Additional spendings derive from increased costs of communication, security consulting, urgent development and testing, and crisis management.
Database security issues tend to accumulate.
If you don’t tend to the safety of your data and DBMS, threats will pile up, compromising your team’s and client’s safety, operations, and resulting in a much bigger breach.
Main Database Security Threats
The main task of database security is dealing with data layer threats. It’s important to understand the risks of storing, transferring, and processing data. Knowing which patterns might jeopardize your safety, you can remove vulnerabilities before they cause an actual accident.
We analyzed the most common database security threats and their specifics: if you are protected from those, you are safe from 99% of all attacks.
Insider threats
It’s the simplest type of a database threat but also the one which is the hardest to predict. Basically, a person who has assigned access to the database and its settings leaks, damages, or deletes information - and there’s a number of ways how it could be done.
-
Malicious intention: someone hijacks the official access to the database - it’s either an employee of the company or an authorized partner;
-
Negligence: a person can accidentally share access to the database via an email or flash drive or after catching a virus.
-
Infiltration: someone enters the team with the purpose of hijacking the company’s data - less common for small and medium businesses, possible for corporations.
The surest way of minimizing the risks of insider attacks is to regularly revisit database security standards and access policies. The company should enable access to the database only for people who need it directly for their work. Employees who no longer work in the company or vendors should not have full permission, if any.

What We Provide
01
Project Design
X Base Cyber Security is a cutting-edge cybersecurity project focused on threat intelligence, risk mitigation, and advanced security architecture. It integrates AI-driven threat detection, blockchain-based data protection, and zero-trust frameworks. Designed for enterprises, it ensures real-time monitoring, proactive defence mechanisms, and compliance adherence, fortifying digital assets against evolving cyber threats.
02
Construction Management
X Base Cyber Security provides specialized cybersecurity solutions for the construction management sector, safeguarding critical infrastructure, project data, and digital assets. We mitigate cyber threats, ensure compliance, and enhance operational resilience through risk assessments, threat intelligence, and secure digital transformation, protecting construction firms from cyberattacks, data breaches, and operational disruptions.
03
Site Evaluation
X Base Cyber Security provides expert site evaluations to assess digital and physical security vulnerabilities. Our comprehensive analysis identifies risks, ensures compliance, and strengthens defenses against cyber threats, safeguarding your organization’s critical assets with cutting-edge security solutions and strategic recommendations.
04
Construction
X Base Cyber Security provides advanced cybersecurity solutions for the construction industry, safeguarding critical infrastructure, networks, and data. We mitigate cyber threats, ensure compliance, and enhance resilience against digital attacks in construction projects.
05
Cost Modeling
X Base Cyber Security's cost modeling evaluates cybersecurity expenses by analyzing risks, infrastructure, and compliance needs. It optimizes budget allocation, ensuring cost-effective protection against threats while maintaining operational efficiency and regulatory adherence.
Our USA Clients







